What is Digital Privacy?
Have you ever CC’d your recipient contacts in an email, rather than using BCC? Connected to unsecured public Wi-Fi networks? Had an advertisement follow you from site to site? Given a game on your smartphone unjustified permission to access your microphone and photos? Posted information online that could allow someone to easily find your home address and phone number?
If you have answered yes to any of these questions, your digital privacy may be at risk. In fact, your information could be used to harm you or the people you contact. Any compromise makes you or your contacts vulnerable to an attack or misuse of information. This is especially true if your organization handles information that could potentially put people’s lives at risk.
As more of our personal and professional lives are lived online, it is important to understand how to protect our communication and data from falling into the wrong hands. To do so effectively, we need to understand two interconnected concepts: digital security and digital privacy. Digital security is about the protection of data and guarding against unauthorized access. Security measures, such as the use of strong passwords, VPNs, and security software, limit who can access certain information. Digital privacy refers to the protection of personally identifiable information, such as names, demographics, addresses, photos, and contact information.
An overlap between digital security and digital privacy is inevitable, since an important part of security is protecting the personal information of individuals in a database. However, here we will focus on digital privacy – why it is important to protect and how to do so. For practical digital security measures, see this digital security checklist.
Why Does It Matter?
Many people believe that privacy is not important to them either because they have nothing to hide or there is nothing they can do about it. Privacy, however, is not about hiding anything but protecting yourself and those around you. If privacy is not protected, any information can be misused to threaten, harm, or bring down the reputation of a person or individual. Private information is private and should not be shared unknowingly.
In an organization, the digital privacy of each individual matters because once the individual’s privacy is breached, it can compromise the security of the entire organization. As we are interconnected in our communication, we can only keep our contacts safe if we protect our personal privacy. A failure to protect your own privacy compromises the privacy of your contacts, organization, and clients.
What could happen to you without sufficient digital privacy?
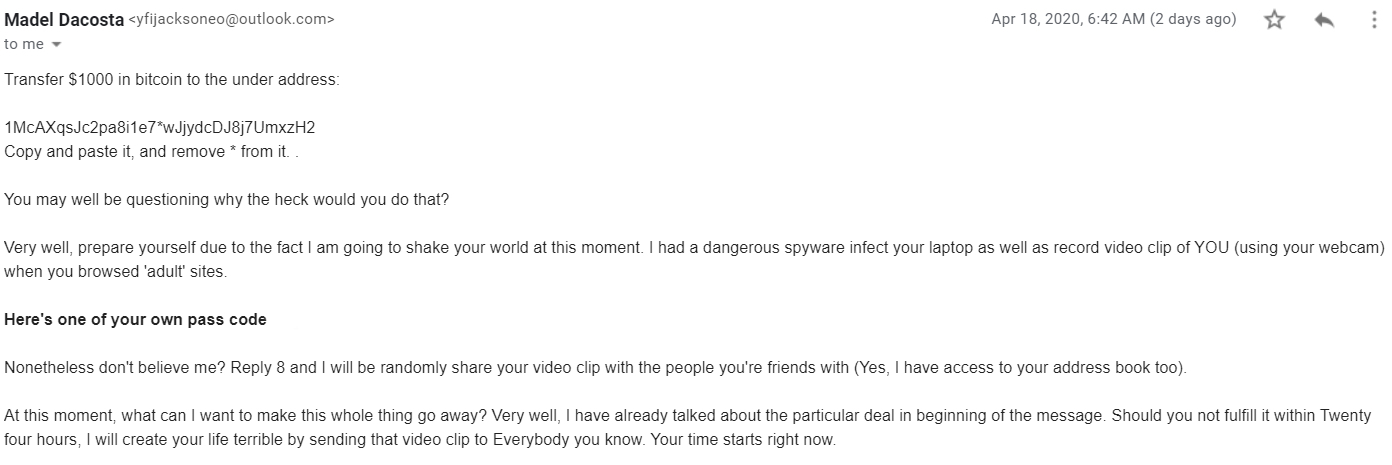
In one instance, a member of a human rights group in South Korea reused the same password for multiple sites, a habit common to many. One website experienced a digital security breach. The attacker claimed to have his password and contact list and threatened to send his browsing history to his contacts if he refused to pay a fee in bitcoin. Once your information has been leaked, intentionally or unintentionally, it cannot be undone. However, it is not too late to begin protecting your information now. If you suspect that you have received a malicious email, you can contact experts at Access Now Digital Security Helpline.
Actual screenshot of the incident
What can human rights documentation groups do?
While there is never 100% protection, there are things you can do to better protect your own and your organization’s privacy. Below are several practical steps you can take to guard your privacy.
Websites
You can control the private information that websites see when you are browsing online. Websites often run scripts and load content from other sites, and share your information with other sites without your knowledge. An example of this is when an ad follows you from site to site. Here are several browser plug-ins that allow you to control what information websites see: Cookie Auto Delete, Privacy Badger, HTTPS Everywhere, No Script, and uBlock Origin. Another thing to be mindful of is websites asking users to accept cookies. Make sure to delete unwanted cookies or use private browsing, in which cookies are automatically deleted upon the closing of the session.
Apps
Apps are another common area in which digital privacy is often breached. It is important to delete any unnecessary apps from your phone and carefully manage permissions. If an app asks for permissions that are not necessary to the function, be cautious about installing it. Has an app asked for permission to access your contact list? This app could knowingly or unknowingly share this information, which, in the case of the dating site/app Ashley Madison leak, potentially exposed the private lives of Canadian government workers.
Email/Social Media
Q: Have you ever CC’d a group of people?
Risk: Anyone with a compromised email account could use that list to target group members into opening a malicious email.
Solution: Use BCC in emails, especially when sending an email to a group of individuals.
Q: Have you ever shared details such as your home address or phone number on your social media profile?
Risk: Such data is private and could be used to target you.
Solution: Be mindful of the information that you share on your social media, especially information that can be used to track or locate you.
Q: Have you checked your social media settings?
Risk: Social media settings are often set to public by default, meaning anyone can see your profile and posts. Content shared on social media is often personal and can be used for malicious purposes.
Solution: Make sure your privacy settings are set appropriately and you know who is in your contact list.
Q: Have you ever used unsecured public Wi-Fi networks?
Risk: Your web traffic connected to that network could be at risk.
Solution: Use secured Wi-Fi networks whenever possible. If it is absolutely necessary to connect to a public Wi-Fi network, use a VPN.
Q: Do you frequently make new online accounts?
Risk: Every time you create an account, you entrust your private information to more people.
Solution: Create a separate email account for online accounts. Create new passwords for each site, using a password manager to keep track.
Q: Have you checked your geolocation settings?
Risk: By keeping your geolocation settings on by default (phone location, camera, delivery apps, social media), you make yourself relatively easy to track, potentially putting yourself and loved ones at risk.
Solution: Review your camera and app geo-tagging functions and turn them off whenever you can. Be mindful of mentioning your location or travel plans in public posts.
Q: Have you confirmed that the video and messaging platforms that you use are secure?
Risk: If you communicate sensitive information over unsecured platforms, you could possibly be giving away that information unknowingly. Even chats with friends and family could be sources of sensitive information.
Solution: Make sure that you use secure platforms, especially when you handle sensitive information. Check out this list for encrypted text and video chat options.
Last Updated: May 26, 2020
Sarah Kim